Security in On-prem Active Directory
November 12, 2024 | by Vebjørn

Contents in this post:
- Introduction
- The issue with Active Directory
- Microsoft Digital Defense Report and ransomware
- Remove or fix?
- Find and mitigate vulnerable configurations
- Security monitoring of Active Directory
Introduction
After years of dealing with ransomware, I want to highlight a critical aspect of these attacks that has been widely discussed among IT security professionals and is a common challenge for many customers, as noted by several security experts.
Active Directory. Good old on-premises Active Directory.
As both customers and their software move towards the cloud, IT departments tend to get stuck in old dependencies “on the ground.” This can be old services, old file servers, or central business software providers who only support on-prem AD, the list goes on. This typically lands the IT department in a “hybrid split” with some cloud and some on-prem.
This in itself is not necessarily a problem, but it can be heavy for an already burdened IT department to now keep track of security on both in the cloud and on-premises.
The issue with Active Directory
Active Directory is the large, central, highly privileged heart of identity and access management in on-premises infrastructure.
Over the years, ever since Active Directory was first adopted by businesses, Microsoft has issued several “advisories” for vulnerabilities that “must be fixed.” Without going into detail, such “advisories” are measures that cannot just be fixed with a Windows update. It requires active configurational changes from the administrator. And the changes have not always been easy to understand or implement (if they were even read at all).
Because of this (and some other reasons), there are now many known and vulnerable configurations in Active Directory that many businesses are vulnerable to without being aware of it!
This, combined with lack of identity maintenance, use of RDP as a management method, and poor password hygiene to name a few things, has resulted in our large, privileged rights heart becoming vulnerable as can be…
This has resulted in the technical legacy in Active Directory being eerily similar across businesses in all industries, and this is the attacker’s dream scenario.

Microsoft Digital Defense Report
Microsoft’s own annual security report reflects this very well in its “Return On Mitigation” matrix.
In the image below, I extracted the top 10 measures from the “Return on Mitigation” list, let’s have a look at number one on top of the list. “Insecure Active Directory Configuration.”

Simply put, the columns in this matrix are the phases of an attack step by step from left to right following the “Mitre Att&ck” framework.
The lesson we note from this diagram is that businesses get a lot of “defense in depth” and security value by addressing Active Directory configuration.
Ransomware
In a classic ransomware attack, the attacker will try to reach the highest privilege in the network, which will typically be the Active Directory “Domain Administrator,” and then spread to all AD-connected devices and servers, and encrypt them.
This means that if you have a domain user who is an administrator on your backup server, and you do not have another offline or external backup…
Encrypted servers, encrypted devices, and encrypted backup. No way back.
Remove or fix?
If the cloud journey is close to complete and can soon cut the hybrid-string to go “full-cloud,” this is absolutely the way to go! But for many businesses, going full-cloud may not be an option just yet for a variety of reasons.
A very good starting point regardless of position is to measure the risk in Active Directory. Here you will find very good support in tools such as “PingCastle.”
“PingCastle” performs a fully automated assessment of Active Directory and compiles this into an easy-to-read report, sorts the remediations into levels, and presents concrete measures with references to data retrieved directly from AD so that it is easy to get started and make the necessary changes!
You also get a pretty risk score that you can show to management, so that the IT department can easily report reduced risk as work is carried out (and to scare the life out of any CISO you may happen upon).
Alternatively, you can use this report to push for phasing out AD dependant services that block the decommissioning of AD.
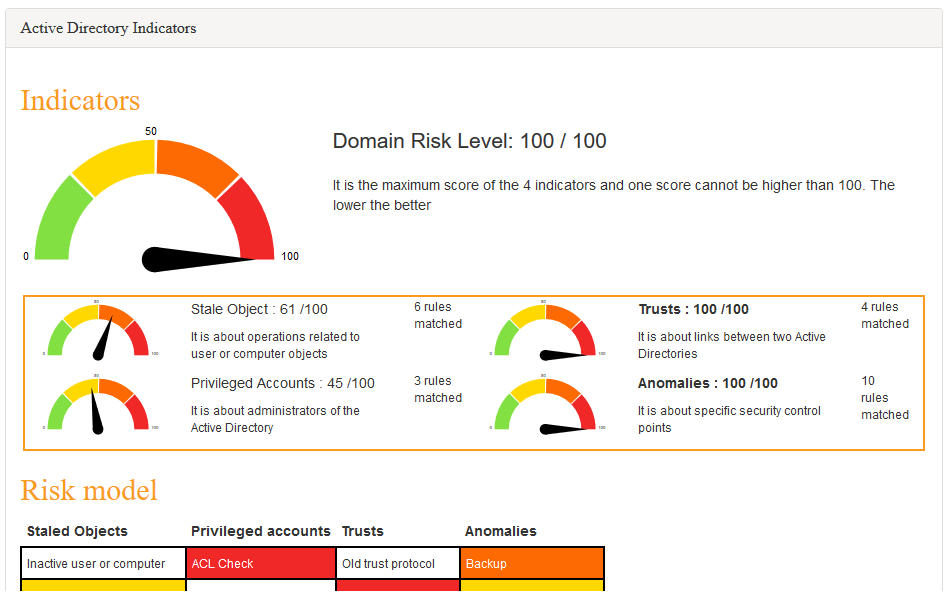
Active Directory is a living thing, so it is wise to run these reports regularly in order to maintain a secure configuration.
Monitoring Active Directory
Defender for Identity (Microsoft 365 E5/A5) is a very good compensating measure if it is difficult to get approval for configuration changes. Production systems are spooky sometimes…
Defender for Identity consists of sensors installed on domain controllers, and possibly ADFS/ADCS servers. Think of this as a tailored protection solution for Active Directory. The product generates logs and alarms that are unique to Active Directory, as well as alarms for the specific methods that attackers use that would not necessarily be detected with other antivirus product or standard EDR software (MDE included!).
This greatly increases the likelihood of detecting and stopping attackers much earlier. Defender for Identity also exists as standalone licenses, but this model often ends up being expensive…
Alternatively, if you do not have an E5/A5 license, it will require a bit more work to detect attacks and malicious activity against Active Directory, but either to get an internal SOC up and running, or an external SOC provider can absolutely cover the necessary detection capabilities through the configuration of sufficient logging.
Contact me or us at Move if you are interested in assistance with anything presented in this article.
We also provide services at Move that cover this. See our website for details.
RELATED POSTS
View all