Defender EASM: Your network perimeter has a flesh-wound…
November 14, 2024 | by Vebjørn
Contents:
1. The nature of service providers and internet exposed assets
2. It is hard to keep inventory
3. What is Defender External Attack Surface Management and how does it work?
4. Harvest practical security value
The nature of service providers and internet exposed assets.
Have you ever used a vulnerability assessment tool like OpenVAS or Nessus against internet exposed services where you provide domains and/or IPs to scan?
Here’s the thing; You (and your IT providers combined) probably have more stuff exposed to the internet than you might be aware of! Plotting in known domains and known IPs in vulnerability scanners will only yield results for the assets that you know that you have.
What about the assets you are unaware of, that are left exposed on the internet?
“What about the stuff that the developer paid for and deployed in Google Cloud?”
This is the part where you say, “WHAT?! We have a GCP Subscription?!”, and someone in the background whispers “Nobody say anything about the AWS farm, the CISO will force me to read the ISMS…”

Yeah… That happens occasionally. But let’s not forget about the third parties.
There are plenty of third-party solution providers that host both new and legacy, and test, and dev, and “temporary legacy dev test in prod” etcetera, on the internet. Even when you exit a partnership with a provider, that doesn’t necessarily mean that they bother removing your services from the internet. If it has a low cost for them, they might just forget it exists. I’ve seen it myself a few times…
And their relation to both “risky port exposure” and vulnerable services varies a lot. Some providers fix vulnerabilities themselves, while other providers have contracts that include waivers for all responsibility for security.
Just like “Phishing”, internet exposed services that are left to rot are a huge risk for initial access. Some of the vulnerabilities that are uncovered to this day astound me in simplicity when it comes to the actual exploitation.
It can be as simple as a line of code you found on GitHub, throw it against a vulnerable asset, and boom. Admin. When exploitation becomes that simple, and the asset is exposed to the internet, I can guarantee you that the bots will compromise the server.
But I’m not here to shame the defenders and IT admins.
It is hard to keep inventory
And it is particularly hard-hitting for companies that have a history of acquisition, as that usually brings along some legacy systems and third-party suppliers, often combined with a loss of company knowledge when IT resources leave for “greener pastures”.
“Documentation? Its in the other sheet of the “passwords.xls” file…” ~Old IT Admin
Static inventories are a lot better than nothing but require constant manual updates. There are solutions for keeping dynamic inventory of assets, which is the optimal solution, but usually, for larger and more complex organizations, maintaining an inclusive and dynamic inventory solution isn’t as easy as one might think…
Imagine running a multi-platform, multi-datacenter, hybrid multi-cloud company with several suppliers hosting servers. Managing such an inventory statically with spreadsheets quickly turns into stale data or burnout.

Resources that are inventoried by EASM are dynamic and exposed to the internet, and I would argue that the exposure of assets against the internet sets a certain risk both for the asset itself, but also potentially for adjacent services reachable from the asset. Defender EASM doesn’t solve the whole inventory issue, but the findings that it does provide are high priority by nature.
In essence, assets that are vulnerable and/or over-exposed to the internet pose a risk to organisations and are by default high priority. EASM can easily find, evaluate and help to highlight and prioritize these issues.
What is Defender EASM and how does it work?
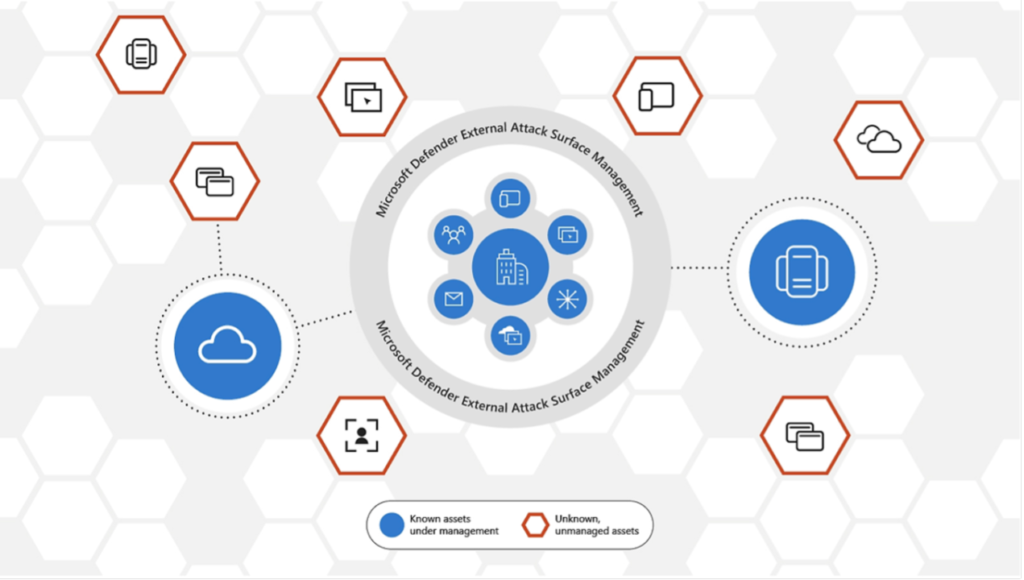
Defender External Attack Surface Management, allows you to input known variables like:
- Company Name(s)
- IP Addresses (or CIDR ranges)
- Domain Names
- ASNs (if you’re that large)
- Email addresses
And the product will dig through the internet every few days to discover and add more and more of your company-related resources, subdomains, hosted services and even third-party hosted services to your inventory. It then charts information like open ports and vulnerabilities related to the discovered assets.
This is all based on open information on the internet, sort of «OSINT»-like, and has no risk for the assets in terms of “load” from scanning.
This information is then aggregated and presented as different dashboards highlighting different risk areas. Here are a few examples:
- Exposed system ports (SSH, Telnet, RDP, SQL, SMB, the list goes on)
- Webpages with login forms using HTTP (without the S)
- Webpages utilising vulnerable software libraries
- Known vulnerabilities for specific products
- «CISA known exploited» list of high priority vulnerabilities
In my experience, going through both the inventory and the dashboard will quickly indicate solutions that “should have been turned off years ago” and show dangerous configurations that are usually easily solvable by IT or the application owners.
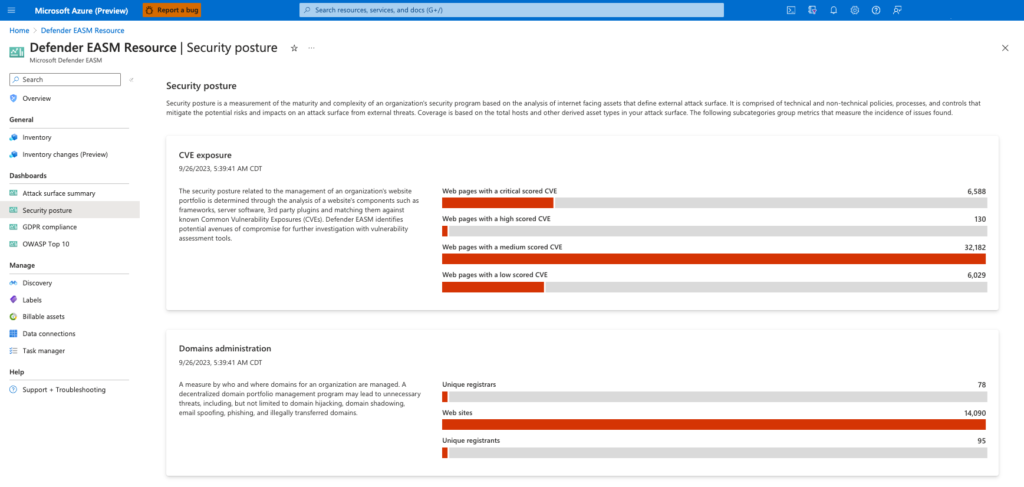
But note: This is not necessarily a replacement for “Web application Scanning” or “vulnerability scanning” tools. This is an exposure management tool.
Harvest practical security value.
EASM shows the attacker’s point of view. Easily targeted misconfigurations or vulnerabilities visible from the entire internet. Solving issues like the ones highlighted by this solution will improve practical security posture.
If new vulnerabilities are found in products included in the EASM inventory, it enables you to discover, react and remediate the issue for example by contacting the supplier, that you also didn’t know that you had, and urge them to apply a security fix.
If someone accidentally expose network port that pose great risks, such as exposing RDP, SSH or other ports for the internet to see, EASM highlights this and enables you to push for the responsible party to close these ports to a specific IP-address as a quick first step to remediation.
In short, finding misconfigurations and vulnerabilities in assets you didn’t know that you had! And fixing it, thereby improving the quality of your perimeter security and information security.
You know, actually avoiding initial access through exposed services.
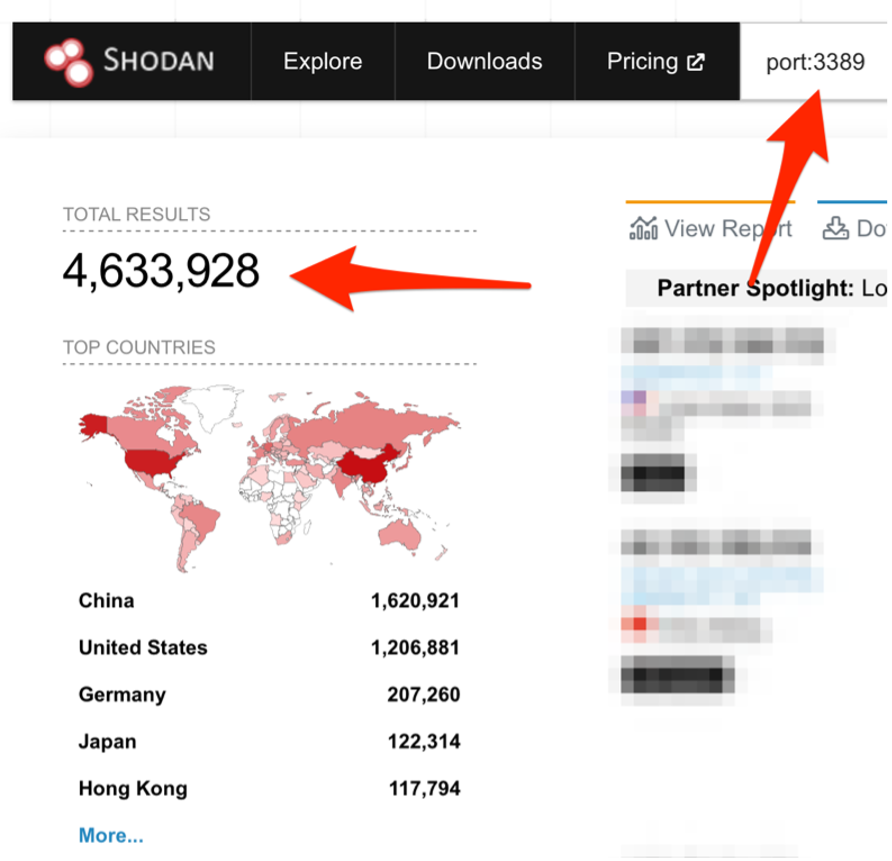
Wanna do a sample test? Check out your own public IPs on Shodan.io for free!
“Who puts RDP on the internet anyway?”
Uhm… A few…
References:
Some sample cases relating to exploitation of exposed services:
1. RDP Brute-Force as an entry way for ransomware: https://www.zscaler.com/blogs/security-research/ransomware-delivered-using-rdp-brute-force-attack
2. SSH Brute-Force as initial access: https://www.bleepingcomputer.com/news/security/new-linux-malware-brute-forces-ssh-servers-to-breach-networks/
3. Fortigate vulnerability used to spread Ransomware: https://www.esentire.com/blog/hackers-exploit-fortinet-devices-to-spread-ransomware-within-corporate-environments-warns-esentire
4. FTP vulnerability used to spread ransomware: https://www.bleepingcomputer.com/news/security/ransomware-attacks-now-target-unpatched-ws-ftp-servers/
EASM Overview:
1. https://learn.microsoft.com/en-us/azure/external-attack-surface-management/overview
RELATED POSTS
View all


